Sinoregal dbAudit Star Regal Database Security Audit System Project
Product Overview - Significance of product development purposes: According to the Verizon Business data leakage investigation report in recent years, 92% of corporate information leakage is confirmed from the database system, and 48% of information stealing comes from internal employees. It can be seen that the biggest threat of corporate data leakage comes from the database. It is imperative to strengthen the security and audit of the database. Based on the above, Xingruig Software has started to develop database-based security protection software from 2015. - Product Brief: Sinoregal dbAudit is an independently operated Database Activity Monitoring (DAM) that records and audits access trajectories of all visited databases and tracks end users without modifying the application. The true identity of the five faces of people, things, time, place, and things (5W). dbAudit is the best choice for companies to prevent database data leakage and compliance. Key indicators DBAUDIT is an independently operated Database Activity Monitoring (DAM) that records and audits the access trajectories of all visited databases and tracks the true identity of end users without modifying the application. Five-oriented tracking of people, things, time, place, and things (5W). DBAUDIT is the best choice for corporate prevention database leaks and compliance regulations. 1. Real-time monitoring of database activities DBAUDIT provides real-time and continuous monitoring and analysis of multiple heterogeneous database activities. Database activities for policy violations can be alerted or blocked in real time, and all tracks can be recorded for post-inquiry analysis. 2. Identify end users and accountability At present, one of the DAM products on the market has a bottleneck that is difficult to break through, that is, it is impossible to identify end users. The general DAM product records the SQL command of the application server to the database server, and its database users. However, today's application system architecture, N-Tier end users mostly use the shared database online or a common account to communicate with the database server, in other words, the SQL cannot be recognized. The real end user to which the command corresponds. To solve this bottleneck, most DAM products must be modified to solve the problem, but for today's enterprises, modifying the application is not only a huge project but also a risk, and most companies will not implement it. DBAUDIT adopts exclusive patented technology. No matter the application system architecture is centralized, master-slave or N-Tier, it can be identified without changing any existing environment, including not modifying the application, installing software in the application system and the end user environment. The true identity of the terminal application system user and the behavior of accessing the database. DBAUDIT records the HTTP/HTTPS access trajectory of the end user and the application server, and uses a special algorithm to compare the access trajectory of the application server and the database server to find out which end user is responsible for each SQL activity, and to achieve accountability. purpose. 3. Product Features - Independent hard device, high stability, no virtual machine (Virtual Machine) - Flexible and expandable architecture for easy installation - real-time monitoring, real-time event alerts - Independent audit, separation of powers and responsibilities - real user tracking - Complete track record for post-tracking - Implement digital signatures to ensure non-repudiation of audit data -Support various regulatory reports - Easy to understand operation - Multiple message pipelines, combined with Security Management Center (SOC) - Graphical report analysis. 4. Support operating system and database Support UNIX, LINUX and Windows operating systems, and can monitor a variety of database products and versions such as Informix, Oracle, DB2, Sybase, MS SQL, MySQL, MariaDB and PostgreSQL. 5. Track monitoring mode The database access can be monitored by DBAUDIT, whether it is on the network or on the local side. The following two monitoring modes are available: - Network listening mode (Sniffer Mode) side recording network access database behavior - Agent records the access behavior of the database local collection 6. System Management - Provide web-based (WEB-Based GUI) management interface, including support for Traditional Chinese, Simplified Chinese and English - Provide management account password security strength setting - Provide system usage track record - Provide online auditing process for abnormal events, flexible customization of signing level and to-do items - Support account role decentralization management, can be divided according to personnel rights and responsibilities, provide different permissions - Provide report sensitive data mask setting function - Provide multiple messaging channels, event notifications can be sent via SMS (SMS), Email, SNMP, Syslog or custom programs - Combined with LDAP authentication system 7. Track record and report - Completely record all user database activities and generate reports, such as DML, DDL, DCL, etc., can completely record the database SQL statement - Support abnormal activity records such as database login failure activities - Support 5W (person, event, time, place, object) track record, including Web users, database users, time (Web login time, database login time, SQL runtime, SQL completion time), SQL statement, parameter values, Return value, return number, error code, source and destination (IP/Port), terminal information, etc. - It can filter the access activity of sensitive forms, and can limit the SQL return value and the pen limit of the record specific table, and can search the return value content in Chinese and English strings. - Support HTTP/HTTPS communication protocol, with Web behavior network side-recording parsing function, record access web page, web page transmission method, web parameter value, web user name, running time - Integrate database transaction auditing software to complete and simultaneously present database transaction SQL command categories and their values ​​before and after the transaction without additional writing programs or database Trigger - Integrate program trace recording software to record the user behavior of the database native operating system level, including the program name, user ID, operation instructions and running time of accessing the database. When the user logs in to the database host in SSH/TELNET/Console mode and uses the UNIX/LINUX SU command to change the identity, the original login user can be automatically recognized. - Audit report provides statistical function 8. Abnormal alarm and notification mechanism -You can set abnormal events, establish warning reports and issue alarm notifications for 5W (person, event, time, place, object) according to your needs. - Provides two kinds of abnormal alarm mechanisms, E-Mail and SMS (SMS), and supports SNMP and Syslog. - Provide black and white list group settings, which can be used to set black and white lists for database users, web users, database client IP, and web client IP. - Support the following alert notifications, including login failures, access to databases during non-working hours, dangerous orders, high-risk group (blacklisted) users, and access to large data bulletins 9. Backup and restore - Support backup encryption - With data encryption and compression function, the data can be backed up to an external storage device by means of FTP and SFTP, and the date or date interval can be specified to restore the backup data to the system. - Provide automatic and manual restore of specified date mode to restore historical backup files as historical track record query 10. Regulation and policy making Includes ISO27001, Basel II, Personal Data Protection Act, Sarbanes-Oxley Act (SOX), Federal Health Insurance Act (HIPPA) for the Medical Industry, Financial Services Modern Law (GLBA) for the Financial Industry, Payment Card Industrial Data Security Standard (PCI-DSS), etc. 11. Audit Statistics Chart and Safety Audit Dashboard (Dashboard) - Provide graphical report analysis functions such as trend, histogram and pie chart - Provide security dashboard function, graphically represent the overall auditing and security status, including the network to receive the amount of packets, the number of SQL included, warning event statistics, audit host CPU, I / O, memory and other use cases - The audit record can be graphically displayed to mine the detailed information of the occurrence of the security anomaly event, and the narrow-range query is gradually drilled down to the record information that triggered the abnormal event. - Can display Top N statistical graphs, selectable for application system, database type, DB server IP, DB server port, DB client IP, DB client port, DB server, database, DB user, OS user, SQL executive, SQL classification, data impact pen count, SQL duration, etc. display statistical graphs, and start and end time intervals of data that can be set for the statistical graph. DBAUDIT product architecture description DBAUDIT has a flexible architecture that provides a variety of modules to meet customer system environments and auditing needs, and supports monitoring of multiple brands of operating systems and databases. Figure 3. DBAUDIT product system architecture diagram DBAUDIT product line description company profile Fujian Xingruig Software Co., Ltd. (hereinafter referred to as Xingruig Software) is a state-owned holding company controlled by Fujian Electronic Information Group. The company was established at the end of 2015 with a registered capital of 150 million. It specializes in safe, reliable and self-controllable domestic database software. Design, research and development, training promotion, sales, operation and maintenance guarantee and professional consulting services for information security software products. In order to deepen the depth of the product line, Star Regal software further introduced the IBM Informix source code, and built the self-controllable Sinoregal domestic database software based on the IBM Informix database source code. The product has passed the safety and reliability certification of China Information Security Certification Center and the quality management system certification. At present, the company's products have great technical advantages in high availability, disaster recovery, spatial data, time series data, etc. At the same time, the company's product support The hardware platform and operating system platform of mainstream manufacturers support the domestic operating system platform better. External Aluminum Foil Reflective Series External Aluminum Foil Reflective Series,Sunshade Net with Grommets,Wind Resistant Outdoor Shade Net,Insulation Sun Shade Curtain Changzhou Green Nets Co.,Ltd. , https://www.czglnets.com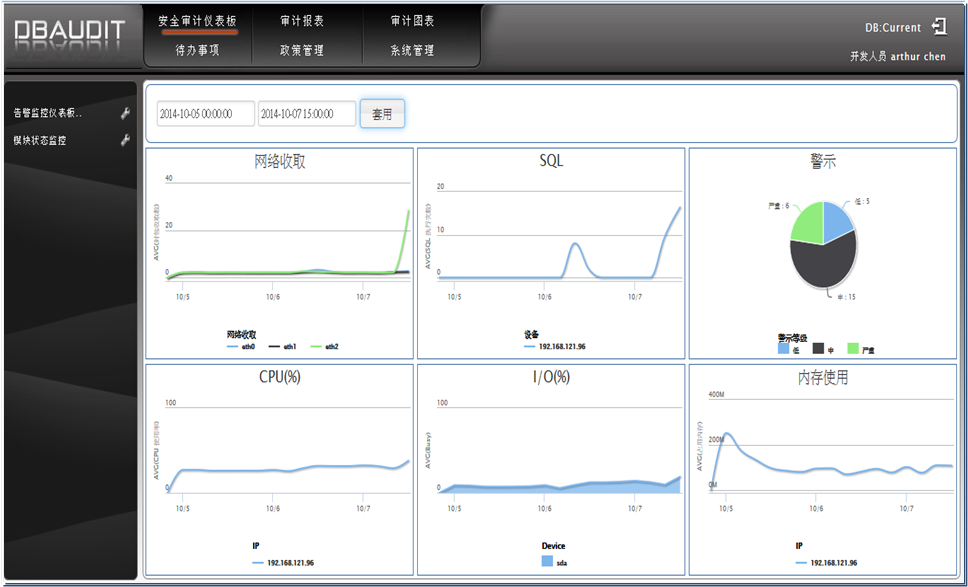
Figure 1. DBAUDIT graphical analysis helps auditors fully understand the overall environmental security status and continue to improve 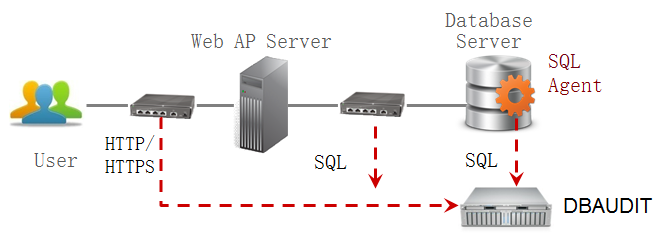
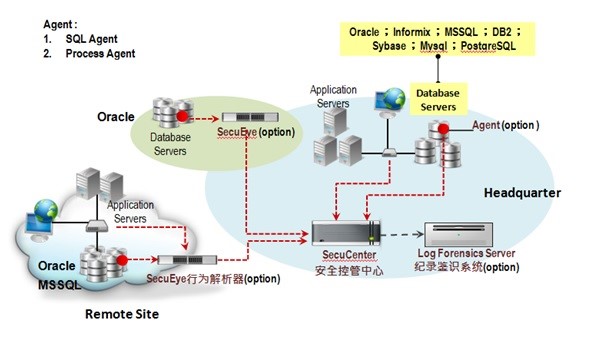
Figure 2. DBAUDIT can collect trace data from the host-side monitoring agent and the network side record.